eDetector
- The new cloud version enables cross-device tracking of forensic analysis results, integrates. AI-powered report generation, and simplifies cybersecurity investigations
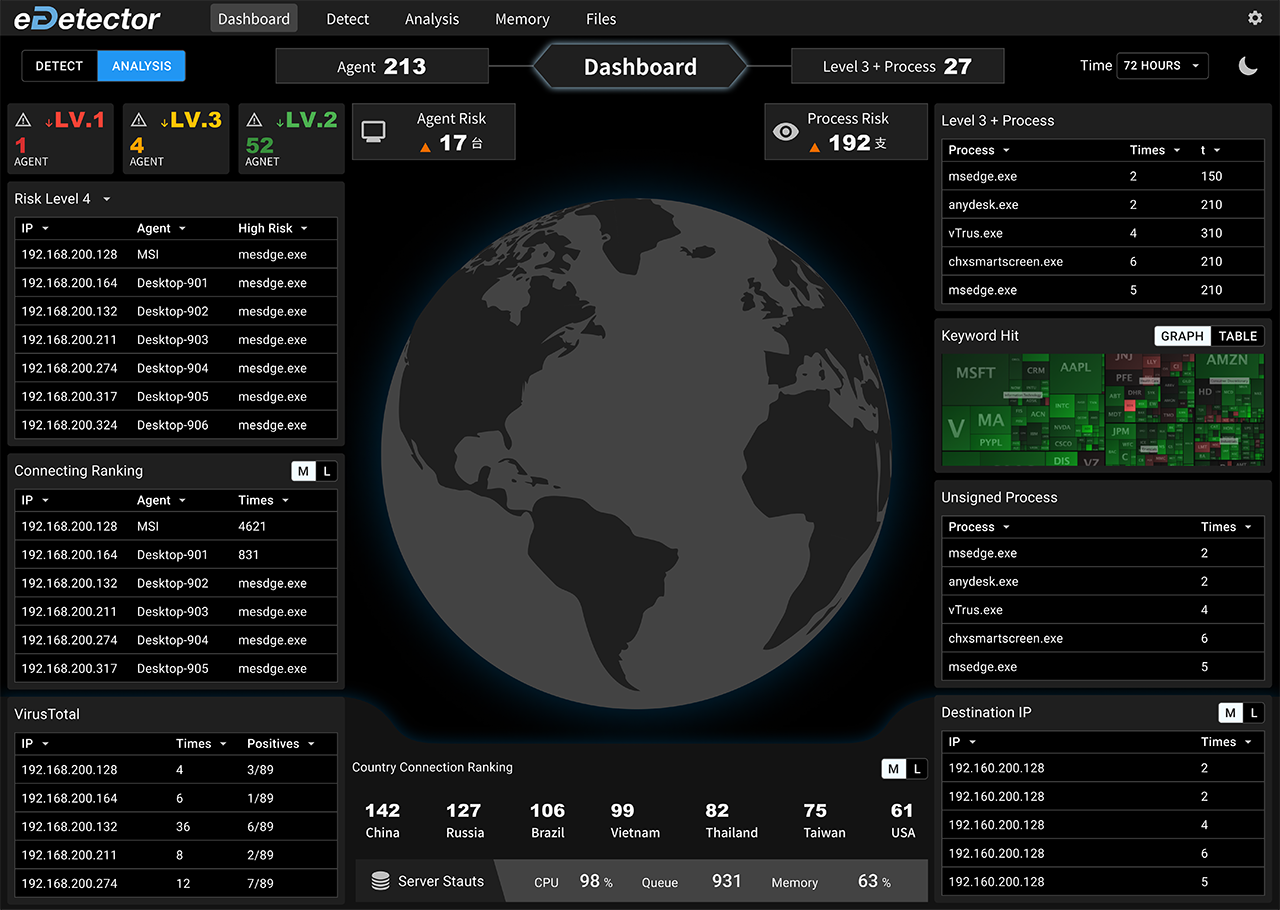
- Large-scale Deployment, Automated Evidence Collection, High-Efficiency Search.
- AI-Powered Automated Report Generation.
- Endpoint Support for Various Windows and Linux Systems to Capture Critical Digital Artifacts.
eDetector is a next-generation endpoint forensic system designed for cybersecurity incident
investigations.
This system has consistently demonstrated excellence in forensic tasks and has been
recognized by
the Small Business Innovation Research (SBIR) program of the Ministry of Economic
Affairs.
With memory detection technology and behavioral trace analysis, eDetector can identify
malicious
activities within memory, including process injection, hidden processes, kernel hooking, and
connection history. It swiftly detects suspicious activities and provides root cause
analysis of
attacks. Through behavior analysis, the system maps process relationships and marks source
IPs,
assisting users in reconstructing the full incident timeline.
By combining advanced technology with intuitive tools, eDetector is a trusted solution for
cybersecurity professionals conducting digital forensic investigations.
- Dual-Mode
Service
Available in cloud and local versions, supporting Windows 10 and 11. The cloud version allows cross-machine management and evidence analysis via a web interface, while the local version supports 64-bit platforms. - Easy Deployment
Quick and simple agent deployment with a one-step installation, supporting simultaneous deployment of up to 500 agents. -
Powerful Evidence Collection and
Search
Supports data collection from Chrome history, USB device info, program network traffic, DNS data, Windows event logs, and more, collecting over 40 types of digital evidence. The efficient search function enables quick retrieval of millions of records with real-time file listings and dynamic data search. - Dynamic Behavior
Analysis
Detects unknown malware through memory analysis and dynamic behavior tracking, creating execution trees, displaying loaded modules, and identifying program links and source IP addresses. - AI and Report Generation
整Integrates AI technologies and VirusTotal for fast report generation, capturing malware signatures and source details. - Yara Scanning
Supports Yara to quickly filter malware signatures and identify potential risks. -
Cloud-Scale Architecture
Stable cloud services with flexible storage expansion, ensuring data confidentiality and availability. Security teams can monitor tasks and progress via a web interface, with a visual timeline for quick data overview.