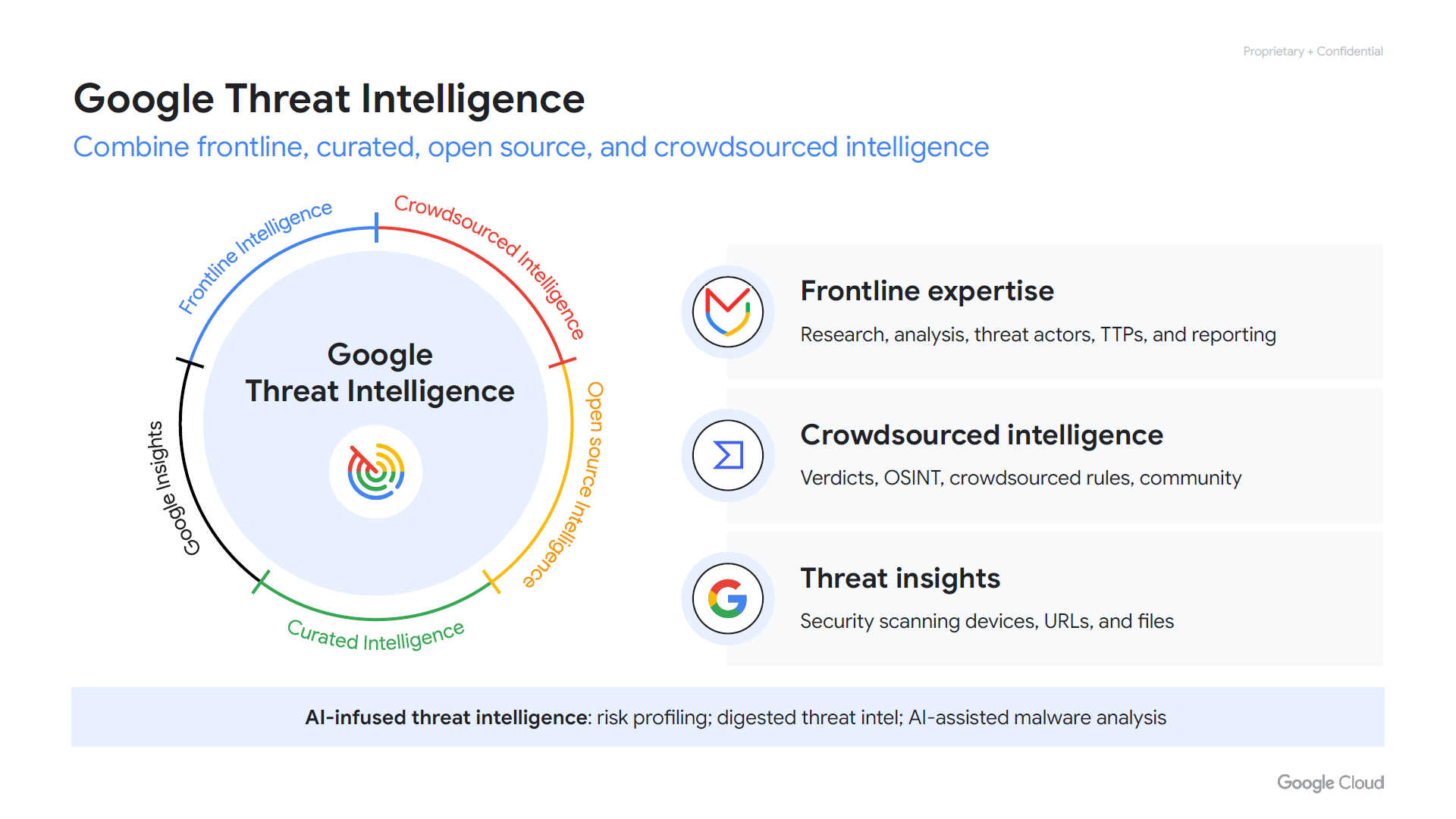
Google Threat Intelligence
- Enrich and extract critical threat intelligence to empower teams in making better security decisions.
- Access IOCs for seamless integration with various security systems, enhancing defense capabilities.
- Automate workflows by leveraging Google Threat Intelligence’s vast dataset via API integration.
- Track malware lineage and threat actors using YARA rules for deeper analysis.
- Leverage an extensive repository of sample data for advanced forensic investigation and threat analysis.
The World's Premier Malware Repository and Threat Intelligence Search Platform.Starting in 2025, Google Threat Intelligence integrates the combined expertise of Mandiant and Google, delivering the most advanced threat intelligence available. It provides a powerful search engine for cybersecurity intelligence, enabling asset inventory, attack surface mapping, correlation analysis, and retrospective threat hunting. With access to a vast malware and organizational knowledge base, it is an essential tool for strengthening cybersecurity defenses, conducting in-depth analysis, and supporting investigations.
Google Threat Intelligence offers a subscription-based cybersecurity
intelligence
solution. For more details, please visit the Google Threat Intelligence
website:Go to Website
The subscription plans are categorized into the following three tiers:
| Plan | Standard | Enterprise | Enterprise Plus |
|---|---|---|---|
| API Request | 5k/day | 30k/day | 500k/day |
| Searches | 10k/month | 100k/month | 100k/month |
| Intel Workbench | N/A | 100 Diff / month,100 Livehunt,25 Retrohunt | 20k Diff / month,20k Livehunt,20k Retrohunt |
| Private Scanning (Files, URLs) | N/A | 100 / month (each) | 1,000 / month (each) |
| Threat Profiles | N/A | 5 Profiles | Unlimited |
| Adversary and Malware Attributions, Vulnerability Intelligence, Finished Reporting | N/A | Included | Included |
| DTM & ASM | OSINT only(Credentials, Domain, Data Leak& 25k Entities | OSINT and Dark Web (Credentials, Domain, Data Leak) Includes custom monitors and dark web research & 500k Entities | OSINT and Dark Web (Credentials, Domain, Data Leak) Includes custom monitors and dark web research & 5m Entities |
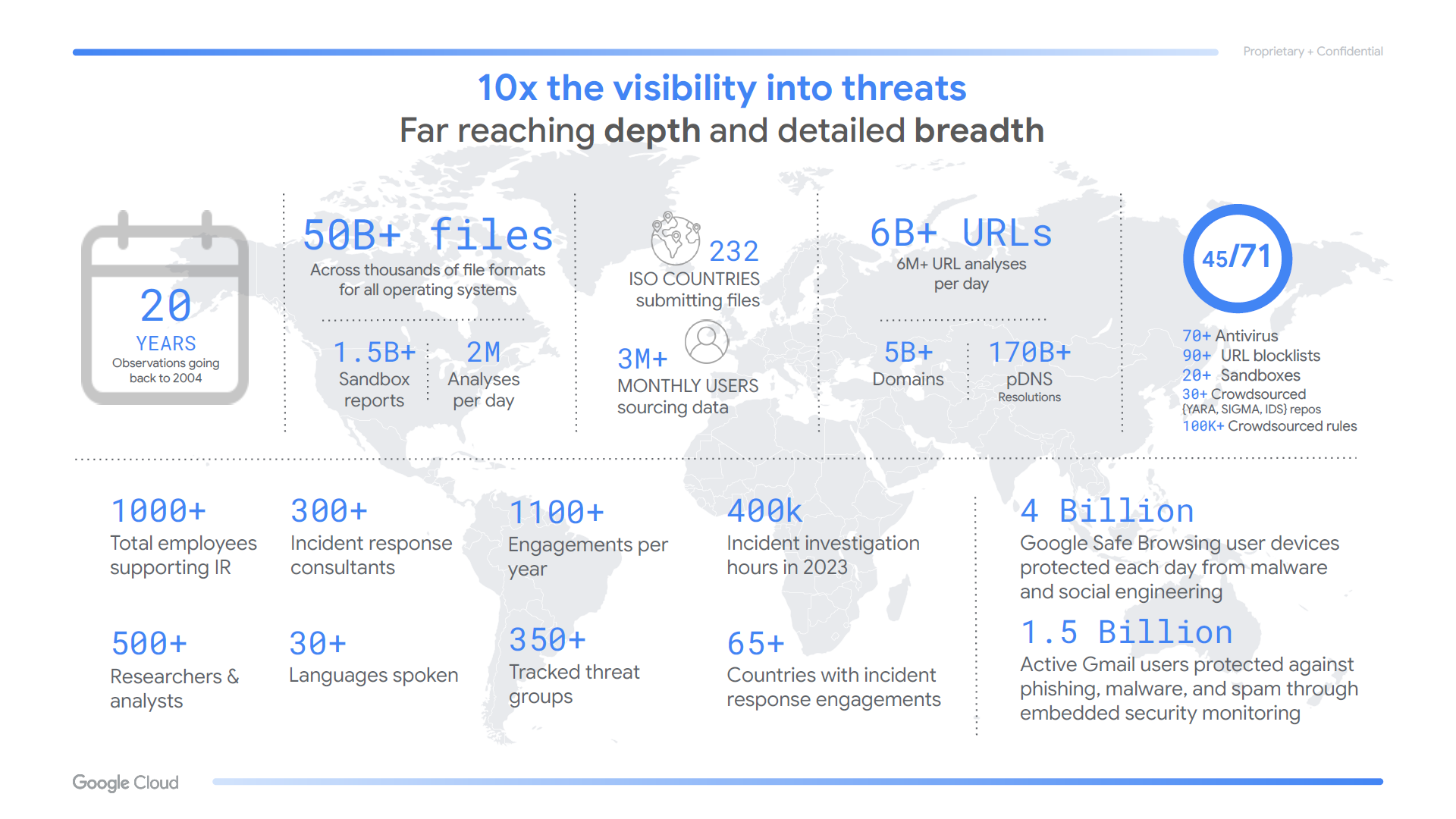
- The Google Threat Intelligence Standard Subscription Includes the
Following Key
Features:
- GTI Searches: Utilize the best-in-class threat intelligence search
engine,
equipped with advanced filtering options to help you quickly find
the
intelligence you need.
- DTM & ASM: DTM (Digital Threat Monitoring) includes publicly
available OSINT
and, in higher-tier plans, extends to dark web intelligence with
monitoring
capabilities. ASM (Attack Surface Management) provides a detailed
asset
inventory, helping organizations identify potential attack surfaces
and
mitigate security risks related to asset mismanagement or Shadow IT.
- API Request: Integrate Google Threat Intelligence API into automated
workflows, enabling seamless interoperability with your existing
security
infrastructure.
For examples and guidelines on integrating with various security devices, please refer to the following link: Visit
- GTI Searches: Utilize the best-in-class threat intelligence search
engine,
equipped with advanced filtering options to help you quickly find
the
intelligence you need.
- In addition to the core features mentioned above, several advanced
capabilities
are available to help save significant time and effort:
Adversary and Malware Attributions, Vulnerability Intelligence, and Finished Reporting provide the following key benefits:- Quickly identify threat actors and organizations behind malicious samples using database insights and crowdsourced intelligence.
- Track specific threat groups and their tactics, techniques, and procedures (TTPs) while accessing relevant toolkits such as YARA, Sigma, and IDS detection rules to monitor ongoing attack campaigns and targeted regions.
- Leverage intelligence from the entire community and partners, enabling faster incident response and investigation through collective security efforts.
- Access real-time global and Mandiant-exclusive threat intelligence reports, export critical findings, and integrate them into existing security infrastructure for enhanced defense.
- Utilize telemetry data to analyze attack patterns, identifying the origin, targeted regions, industries, and attack timeframes.
- Commonalities analysis helps detect similarities between threats,
allowing
proactive mitigation and detection of attack campaigns.
- Intel Workbench (Livehunt): Automatically applies custom YARA rules to detect and notify users of matching samples in real-time.
- Intel Workbench (Retrohunt): Conducts historical searches across the
threat
intelligence database using custom YARA rules, identifying past
occurrences
and providing relevant results.
- Feeds: Through API integration, Google Threat Intelligence enables
organizations
to transform its extensive intelligence database into an on-premise
asset from
the start of the subscription. This feature is ideal for large-scale
defense,
national security, government agencies, and enterprises looking to build
their
own intelligence repositories.
The available Feed types include:
- C2 Feed
- Ransomware Feed
- Additional feeds to be announced by the provider… (For more details, please contact us.)
- Private Scanning (Files, URLs): Through Google Threat Intelligence’s extensive malware identification expertise, files can be scanned without being shared or publicly disclosed. This feature is ideal for scanning sensitive data or files that should remain inaccessible to external parties. For more details, please refer to the following link:Go to